About Us
Gamutech is built and developed together by experienced young professionals to provide the best solutions for each of our clients.
With more than 15 years of software development & CyberSecurity experience we offer quality, timely and affordable software development & CyberSecurity.
We excelled in building custom application, information system & CyberSecurity. We work closely with various clients, from small and medium-sized business, to enterprise corporations and public sectors.
Our working culture and team will help you to form a well-designed architecture, develop a suitable business process, and wrap it with a beautiful, dynamic, and intuitive User eXperience.
Our Services
Focused on delivery of IT & Digital Services, we help our clients meet their needs to increase their productivity and security.
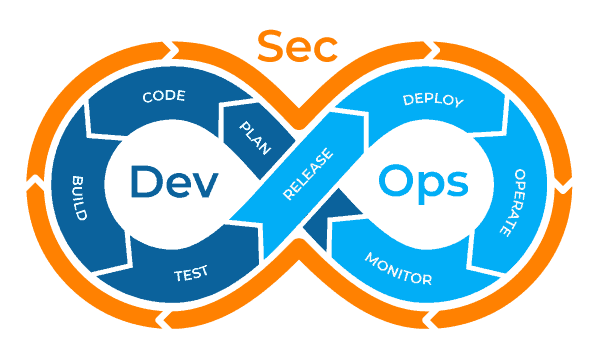
DevSecOps
The goal of DevSecOps is to continuously build, test, and deliver secure software at high speed, using automation and collaboration between development, security, and operations teams. This approach can help organizations to develop and deploy software more quickly and efficiently, while also reducing the risk of security vulnerabilities and incidents.
Infrastructure
IT infrastructure refers to the physical and virtual resources that are used to build, operate, and maintain an organization's information technology (IT) systems. These resources can include hardware components such as servers, routers, and switches, as well as software applications, network and storage systems, data centers, and other facilities.

Penetration Test
A pentest, or penetration test, is a simulated cyber attack on a computer system, network, or web application. The goal of a pentest is to identify security vulnerabilities that an attacker could exploit.

Vulnerability Management
Vulnerability management is the process of identifying, classifying, prioritizing, and mitigating vulnerabilities in computer systems, networks, and web applications. Vulnerability management is an ongoing process that involves several steps.

Risk Audit
A risk audit is an examination of an organization's risks, including both the likelihood of those risks occurring and the potential impact if they do. The goal of a risk audit is to identify areas where the organization is vulnerable, and to recommend steps that can be taken to reduce or mitigate those risks.

SOC & Incident Response
Incident response is the process of responding to a security incident or breach. It involves a set of activities that are carried out in a coordinated and systematic manner to contain the incident, investigate its root cause, and prevent it from happening again in the future.
Call To Action
You have vision. We have team to get you there.